Multifactor Authentication (MFA)
Atualizado/Updated: 2025-03-18
Multi-factor authentication (MFA) is an electronic authentication method in which users confirm their identity by presenting two or more pieces of evidence successfully. In ISCTE we consider your username and password to be the first factor of authentication.
We recommend the OKTA Verify application as a second authentication factor:
Set up the Okta Verify app (Preferred)
- Go to https://login.iscte-iul.pt.
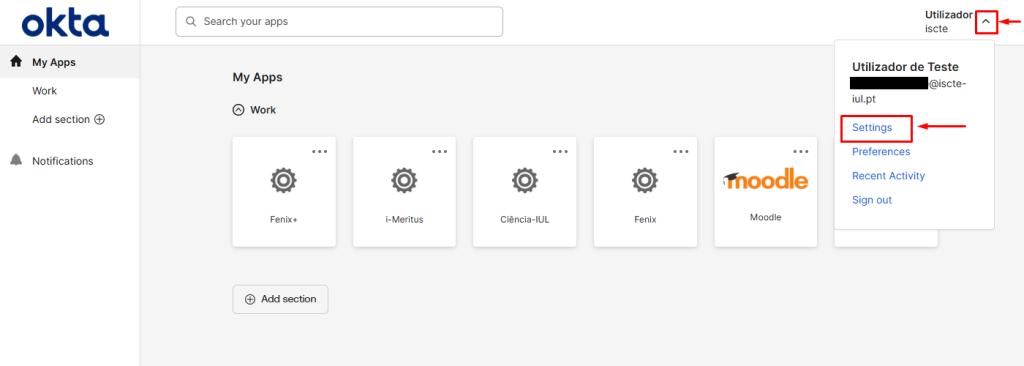
In the top right corner, click on the downward pointing arrow and then on “Settings“.
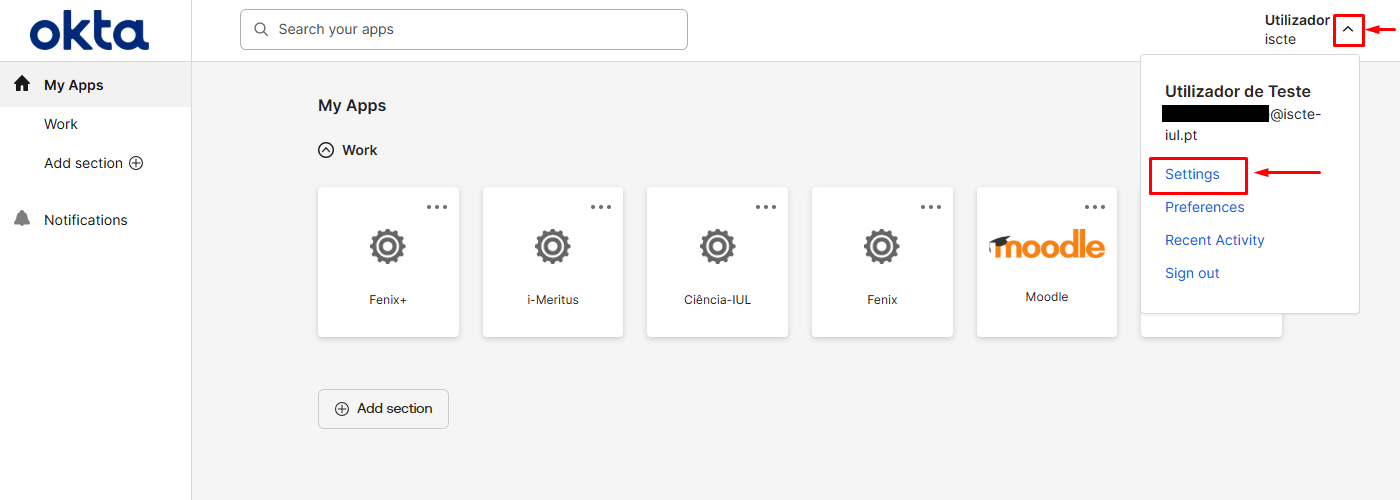
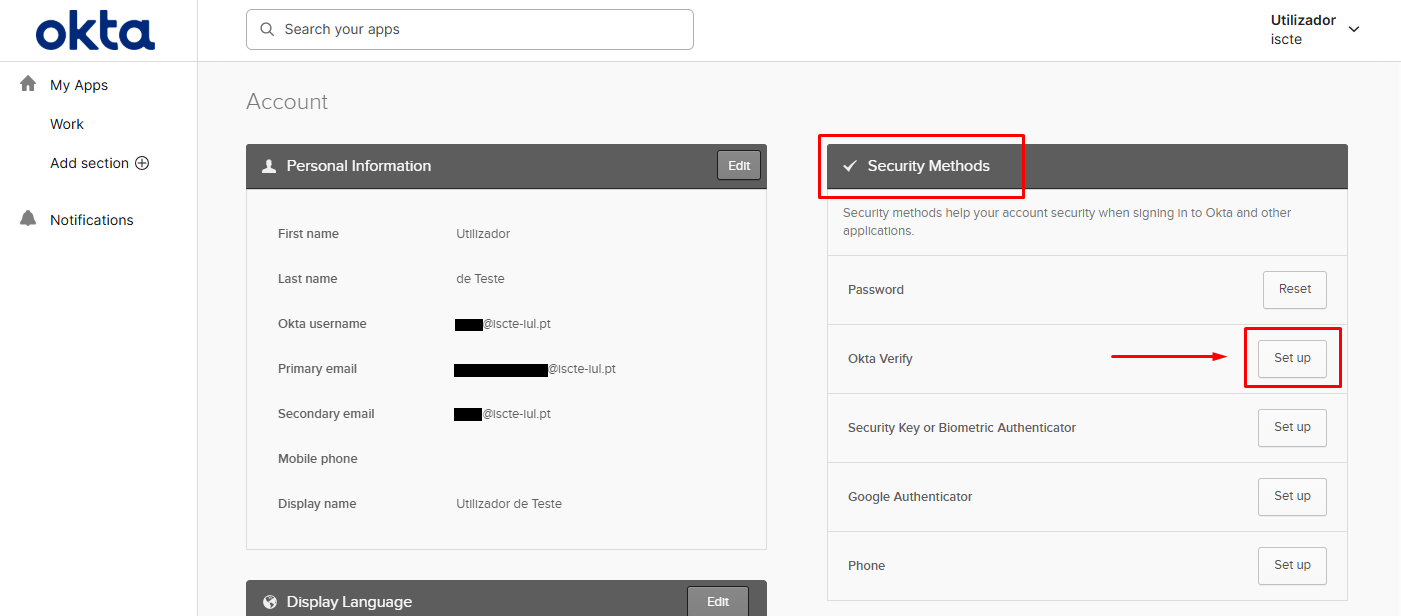
- If you prefer to use the OKTA Verify app, in the “Security Methods” field, click on “Set up” placed in front of “Okta Verify“.
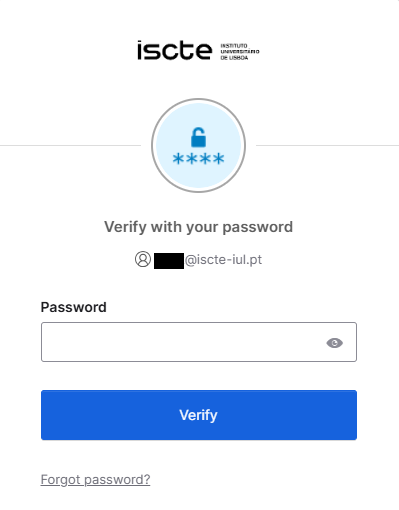
- Fill in your ISCTE password.
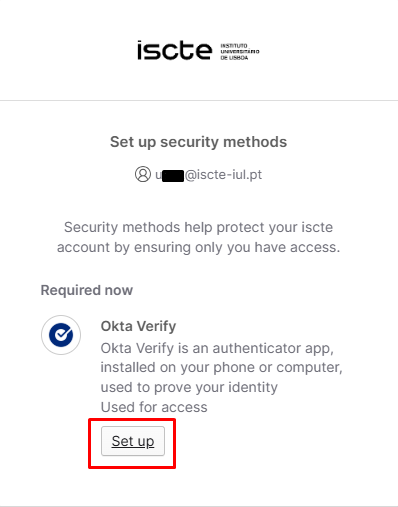
- After filling in your password, click on Set up as in the image below.
- A QR code will be displayed.
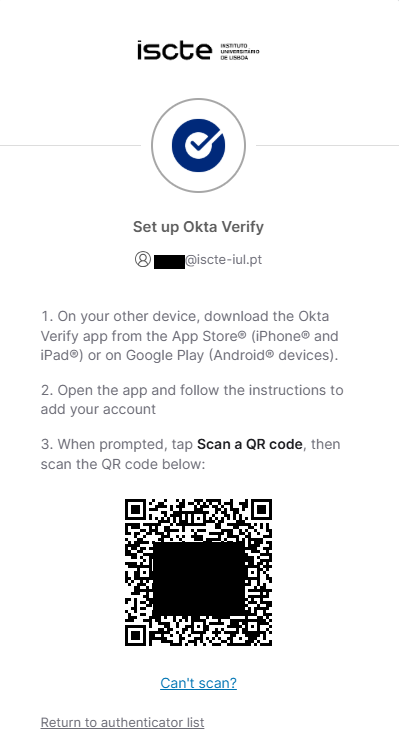
- Install in your smartphone the Okta Verify app from the Google Play store/App Store.
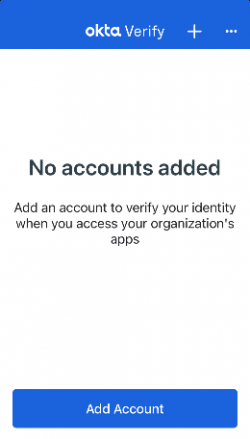
When you open the app, you will see the screen on the right. Click on “Add account”.
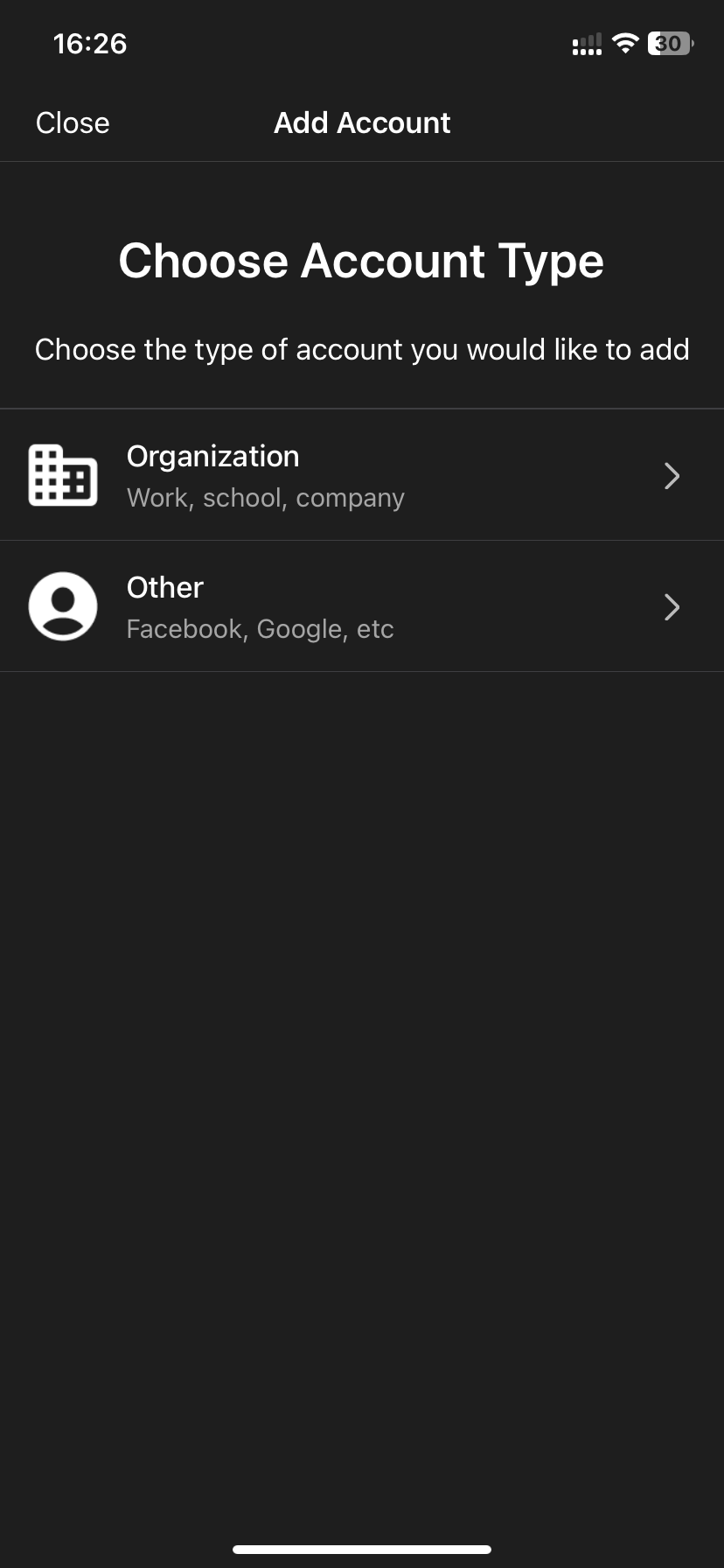
- Choose organization as the account type. When the app asks if you want to “Add Account from another device”, click “Skip“.
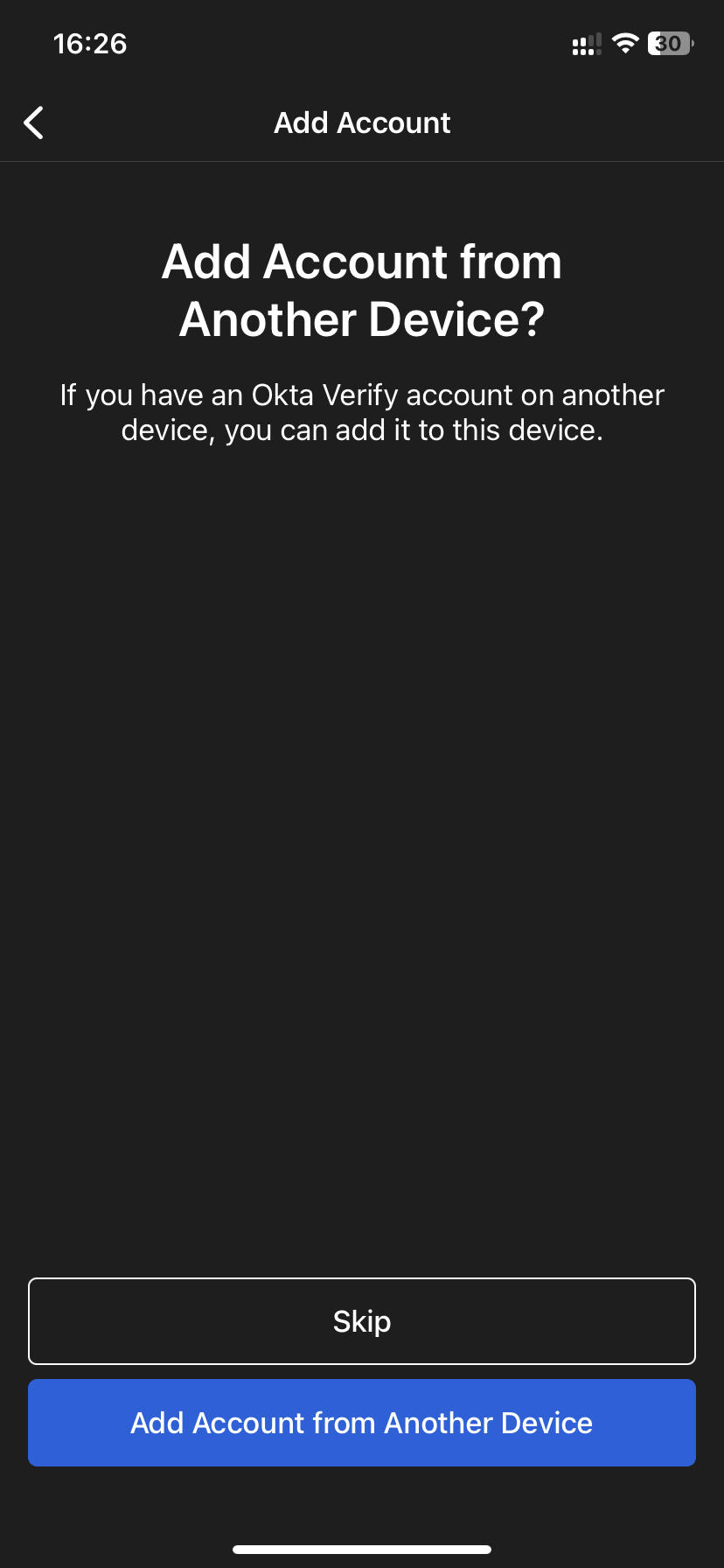
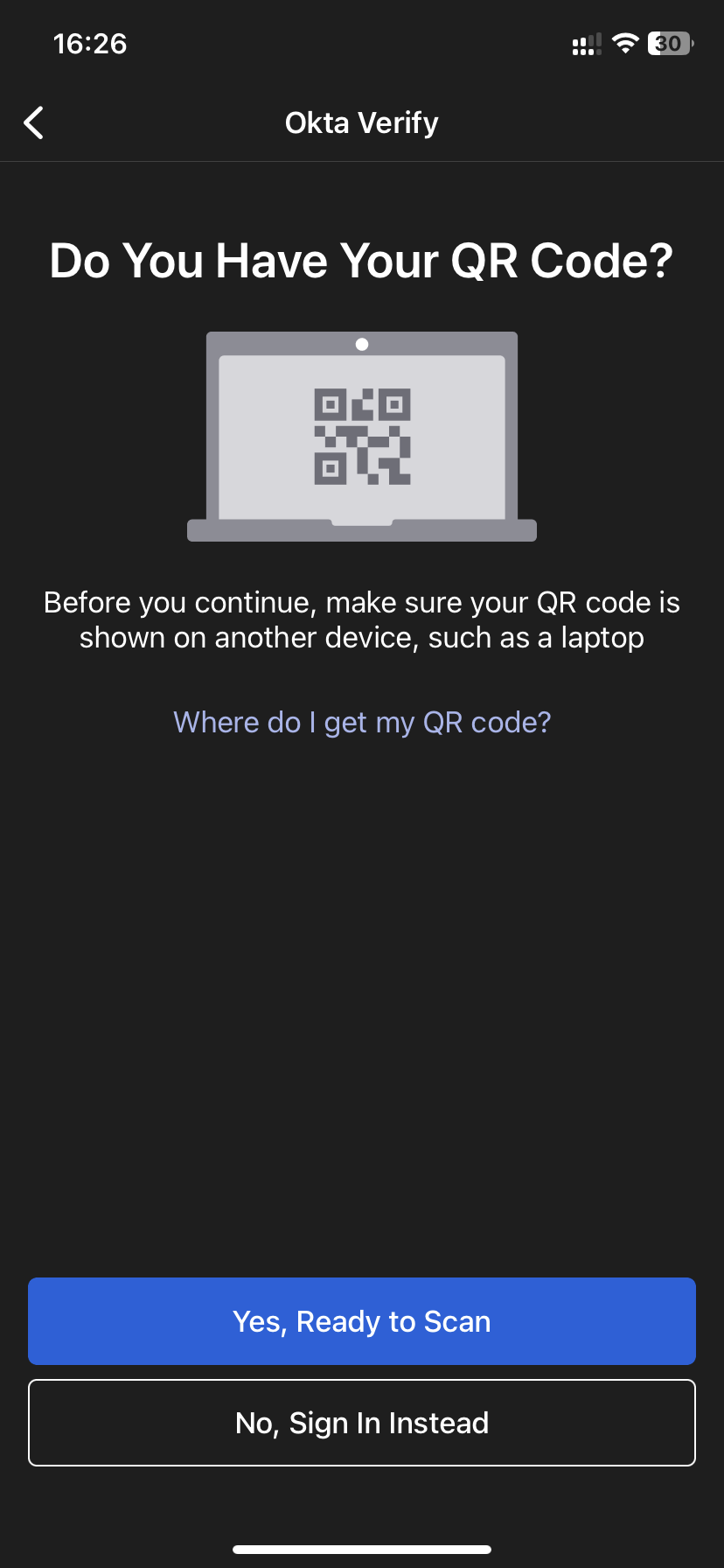
- Then click on “Yes, Ready to Scan” and scan the QR code shown to you on the OKTA website (see paragraph 5).
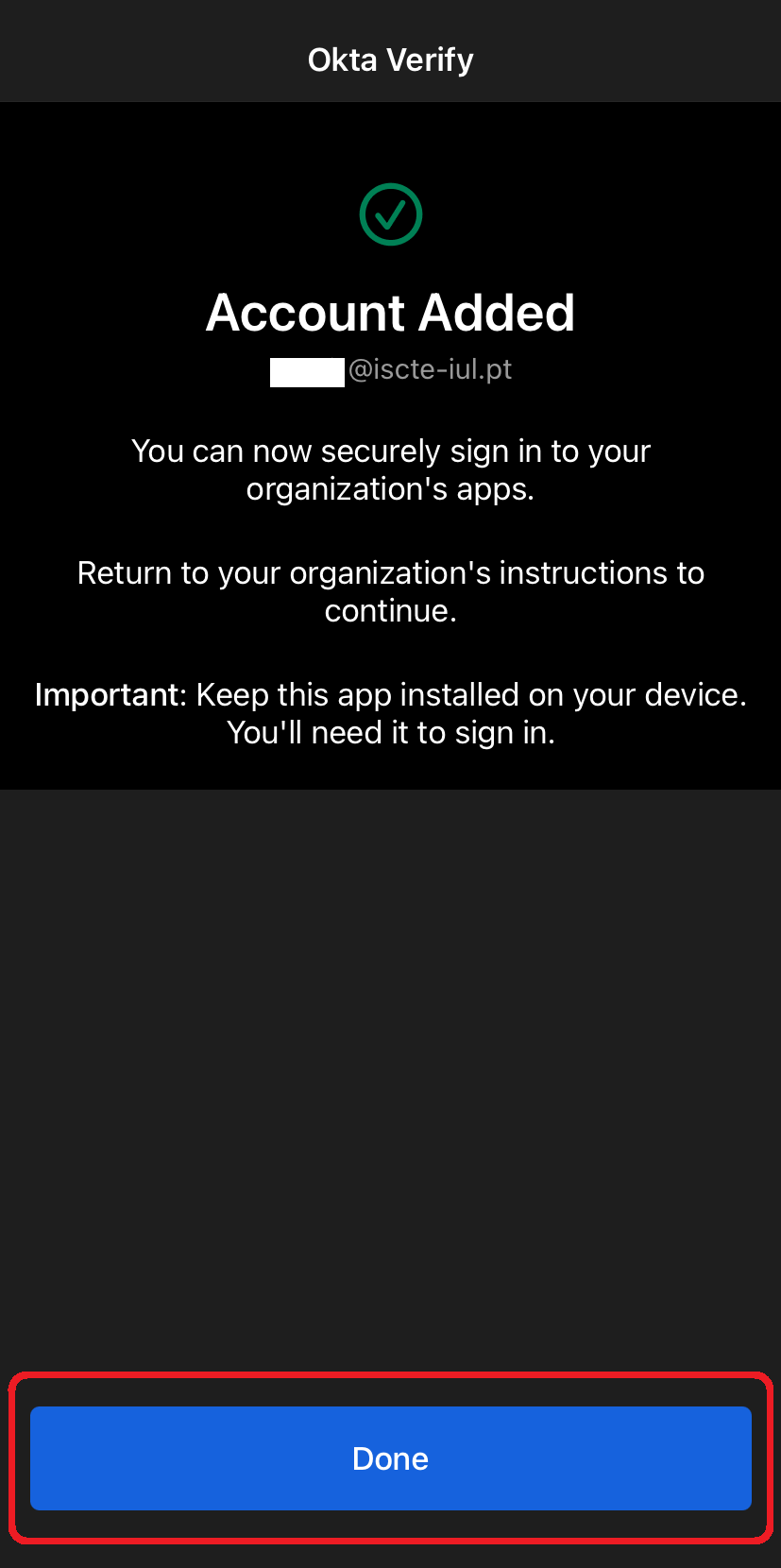
- After scanning the code, confirmation should appear that the account has been added to Okta Verify.
Click on “Verify”.
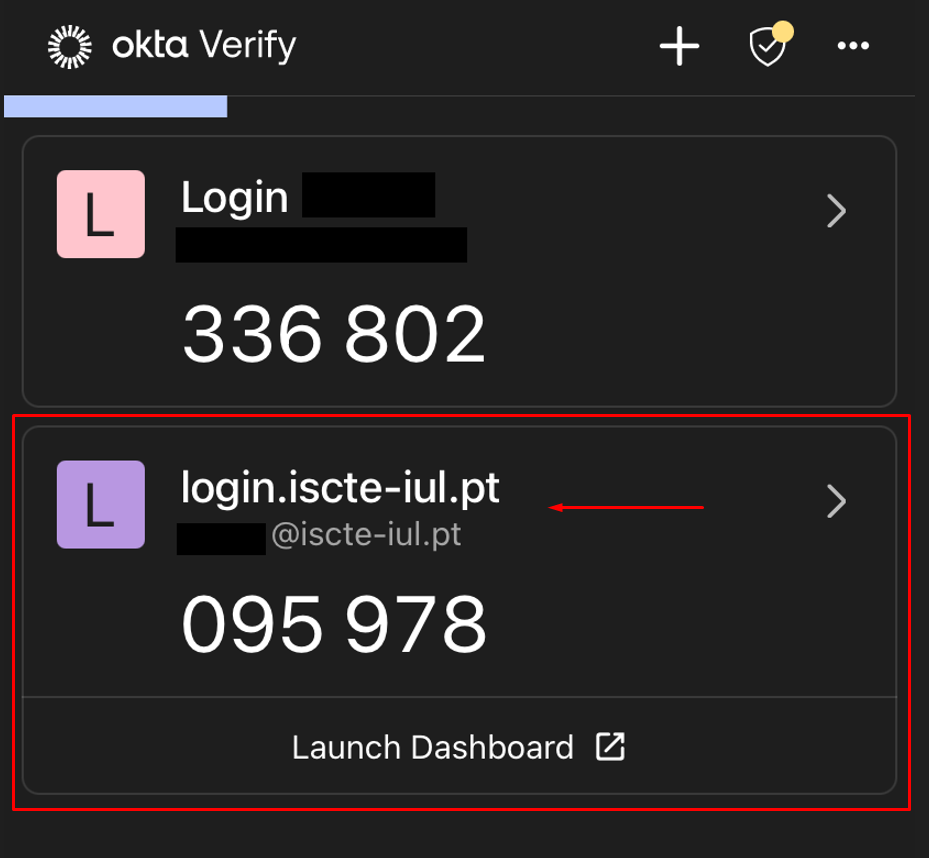
- From now on, you can use multi-factor authentication via push notification on your device or using temporary 6-digit codes that appear in the app (see image below).
Other methods (not recommended)
As an alternative to the application recommended by our service (Okta Verify), you can also choose among:
- Go to https://login.iscte-iul.pt.
In the top right corner, click on the downward pointing arrow and then on “Settings“.
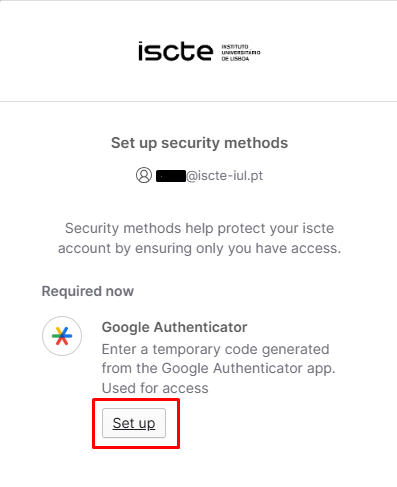
- If you prefer to use Google Authenticator or similar applications*, in the “Security Methods” field, click on “Set up” placed in front of “Google Authenticator“.
* For similar TOTP (time-based one-time password) or authenticator apps, you should always select the Google Authenticator option.
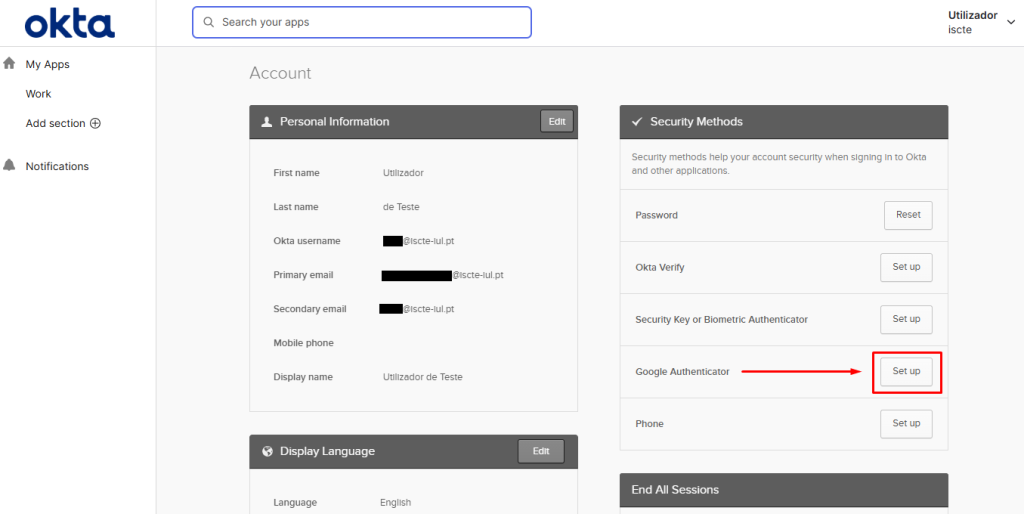
- Fill in your ISCTE password.

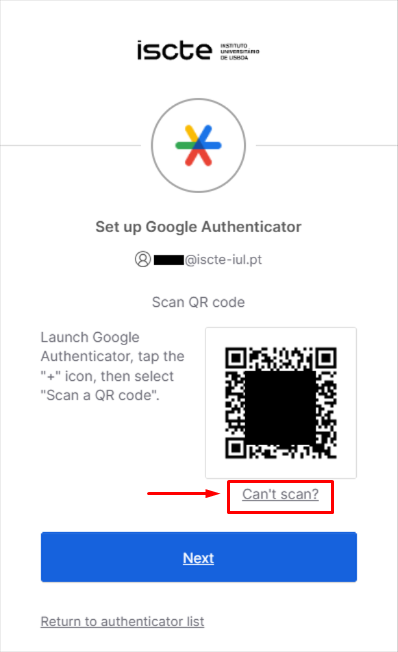
- After filling in your password, click on Set up as in the image below.
- A QR code will be displayed.
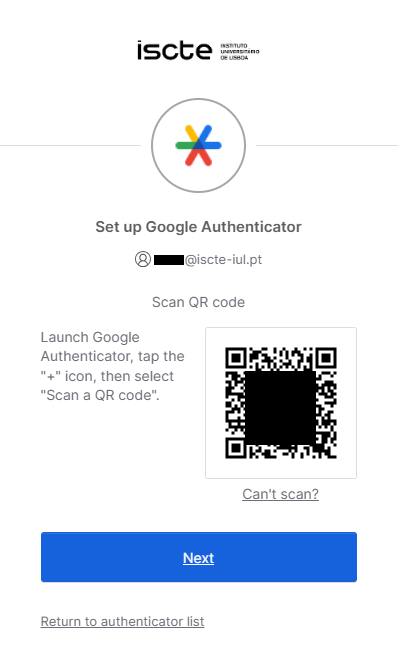
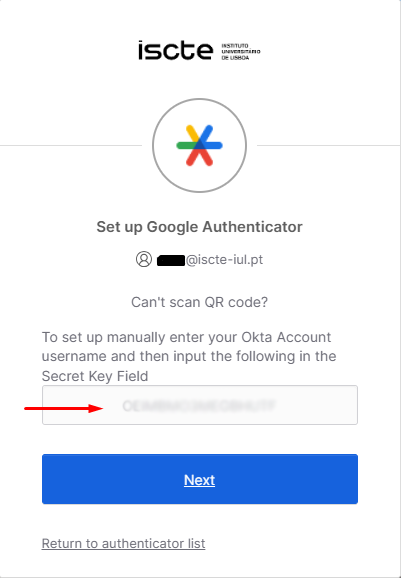
If you can’t scan the QR code and use another type of TOTP application, click on “Can’t scan?” and use the code that appears on the next page.
- Install the Google Authenticator application or similar on your mobile phone from the Google Play store/App Store.
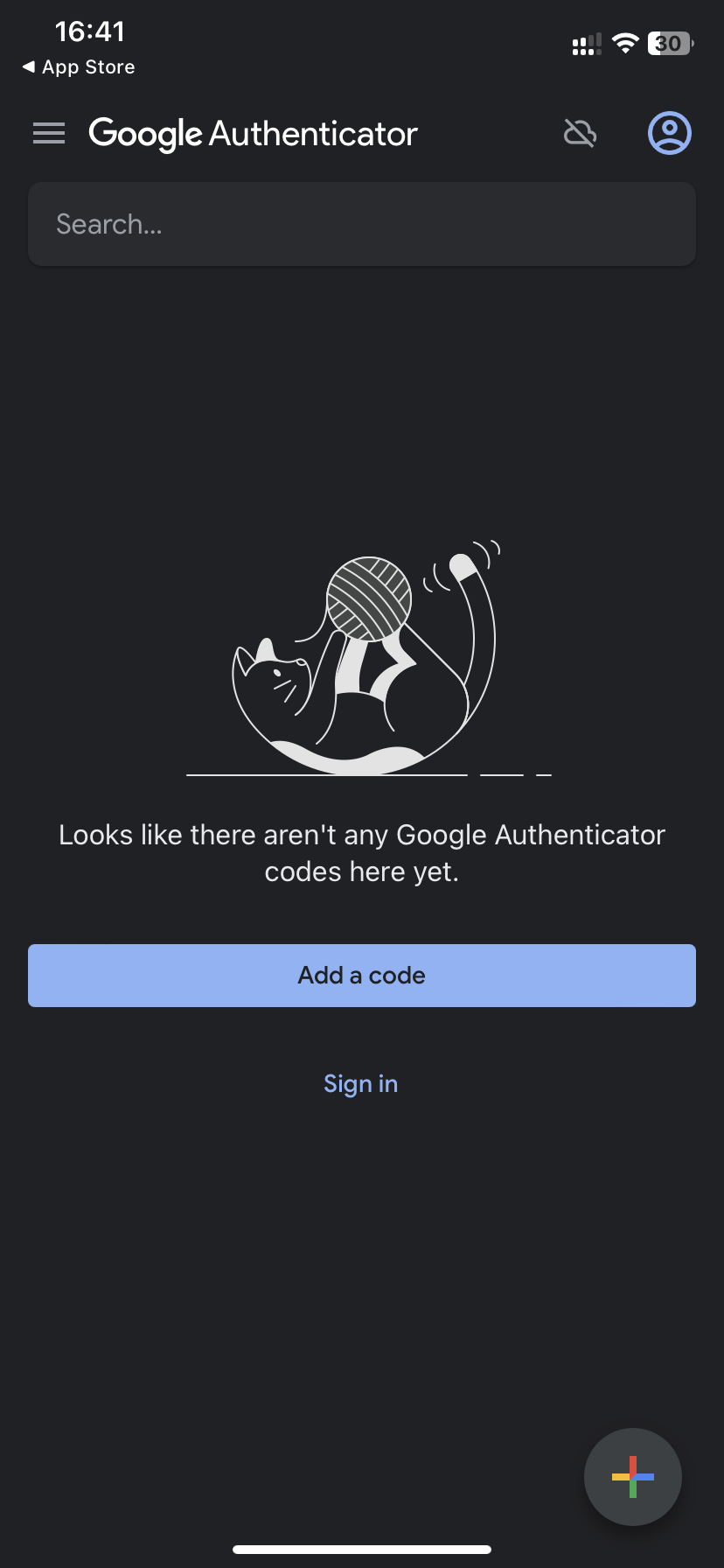
When you open the application you will see the screen on the right and click on “Add a code”.
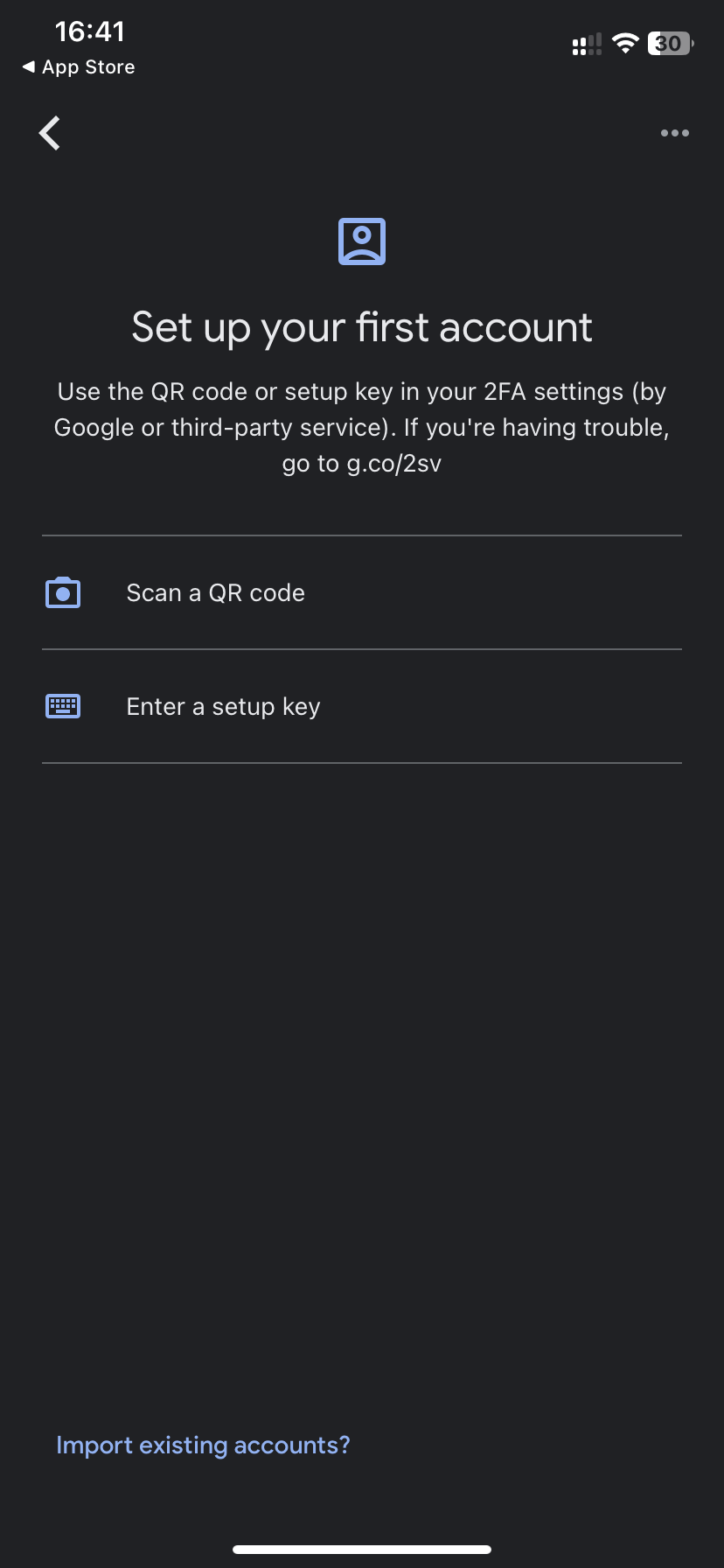
- Then click on “Scan a QR code” and scan the QR code shown to you on the OKTA website (see paragraph 5).
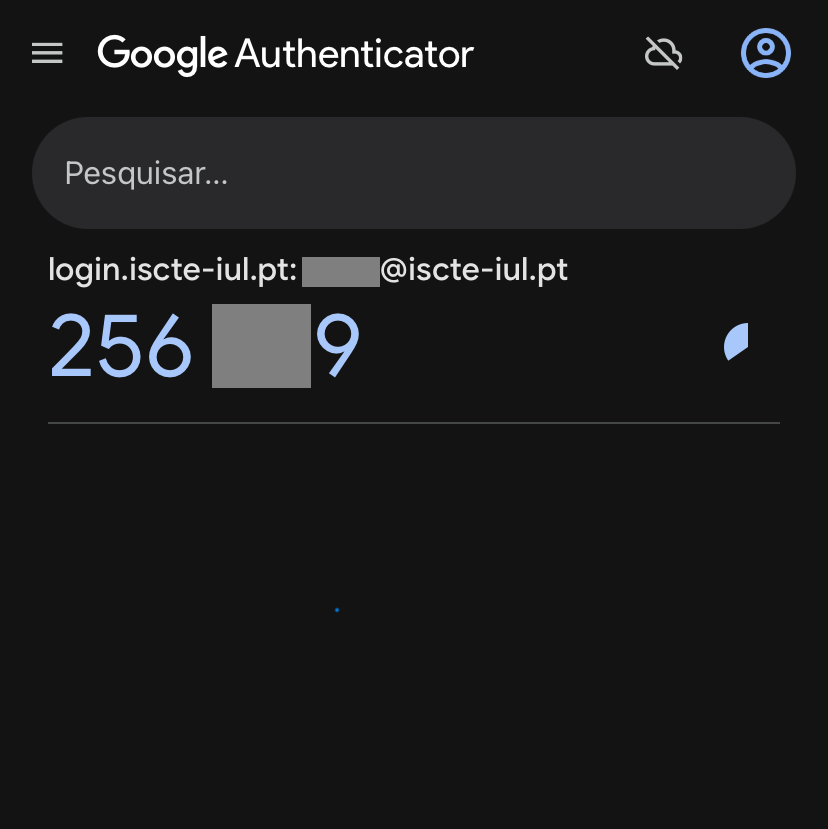
- After scanning the QR code, your login.iscte-iul.pt account will appear in the mobile application with an associated temporary code.
- On the website (see paragraph 5), click on “Next”.
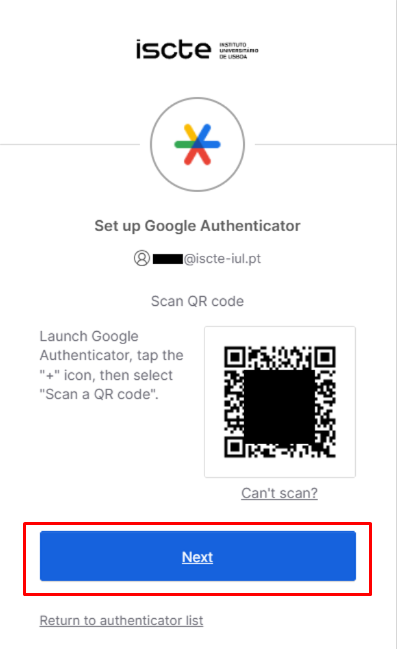
- From now on, you can use multi-factor authentication on your device using temporary 6-digit codes that appear in the app.
The configuration is finished and you will be redirected to the login.iscte-iul.pt page.
- If you prefer to use the Security Key FIDO/U2F, go to https://login.iscte-iul.pt.
In the top right corner, click on the downward pointing arrow and then on “Settings“.

- Click on “Set up” under “Security methods“, in front of “Security key or biometric authenticator”.
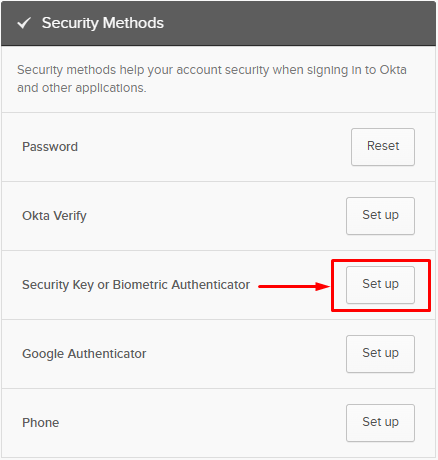
- Fill in your Iscte password.

- After entering your password, click on “Set up” as in the image below.
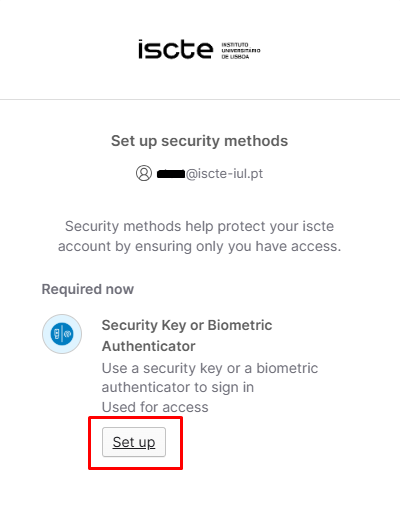
- When choosing the type of configuration, press “Set up“.
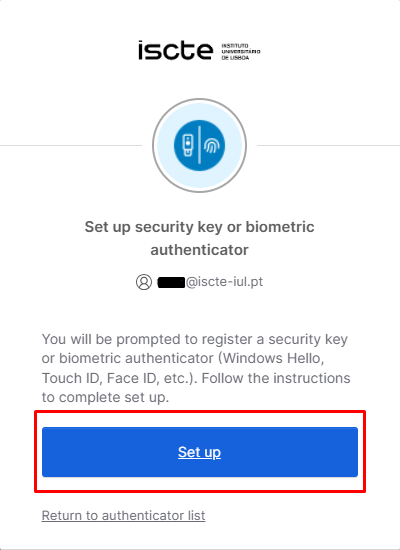
- Click “OK” to configure the security key for authentication.
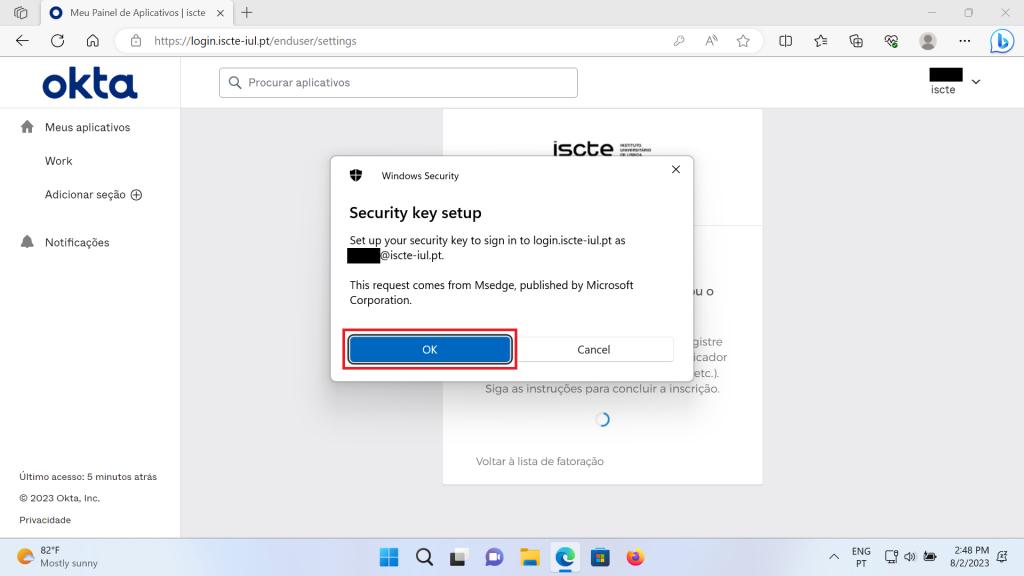
- Click “OK” again to allow the key to be identified.
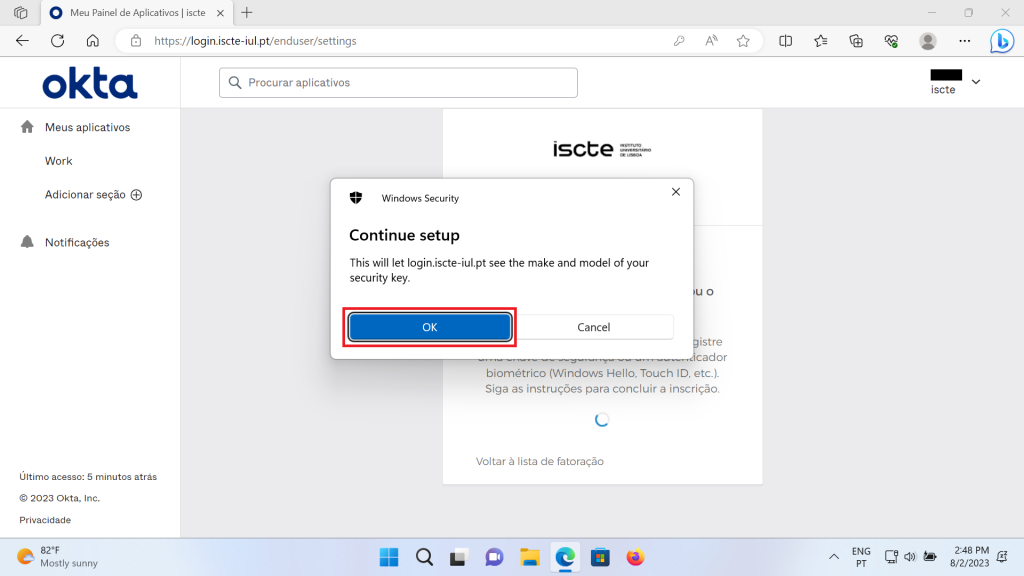
- Insert the security key into the USB port of your computer.
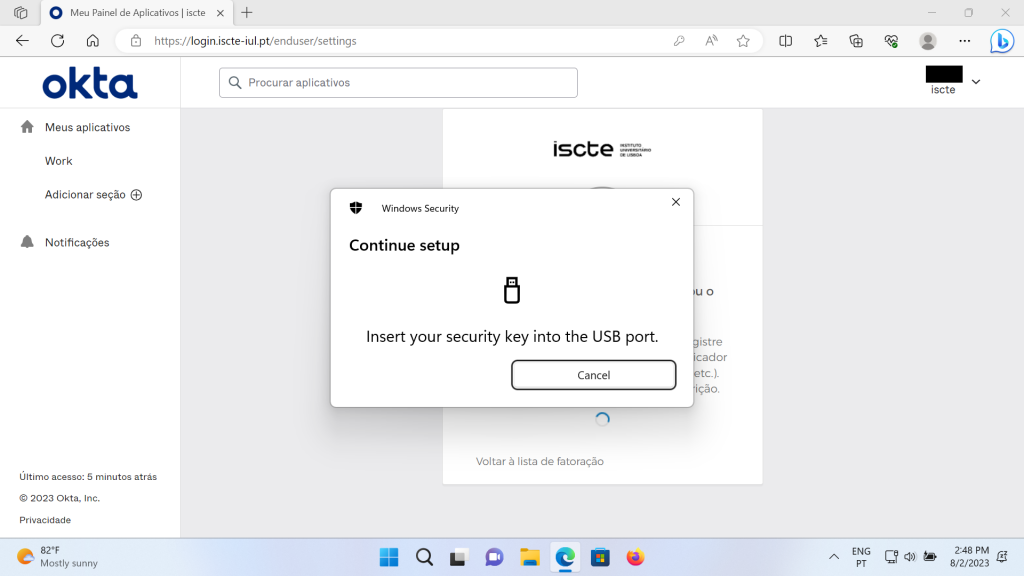
- When the key will be detected by the system, you will need to create a PIN to use with the security key.
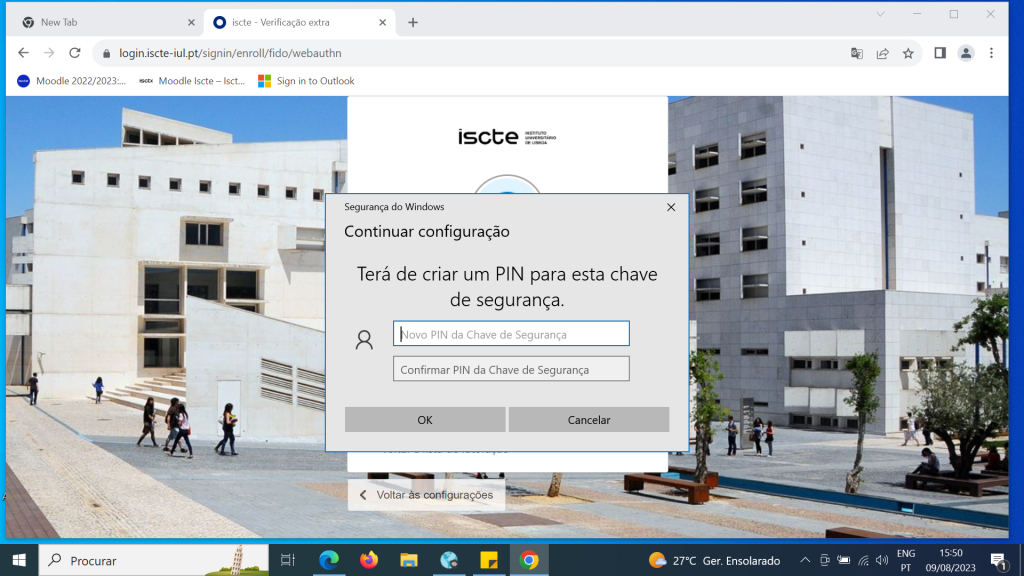
- After that, you should place your finger on the security key’s button.
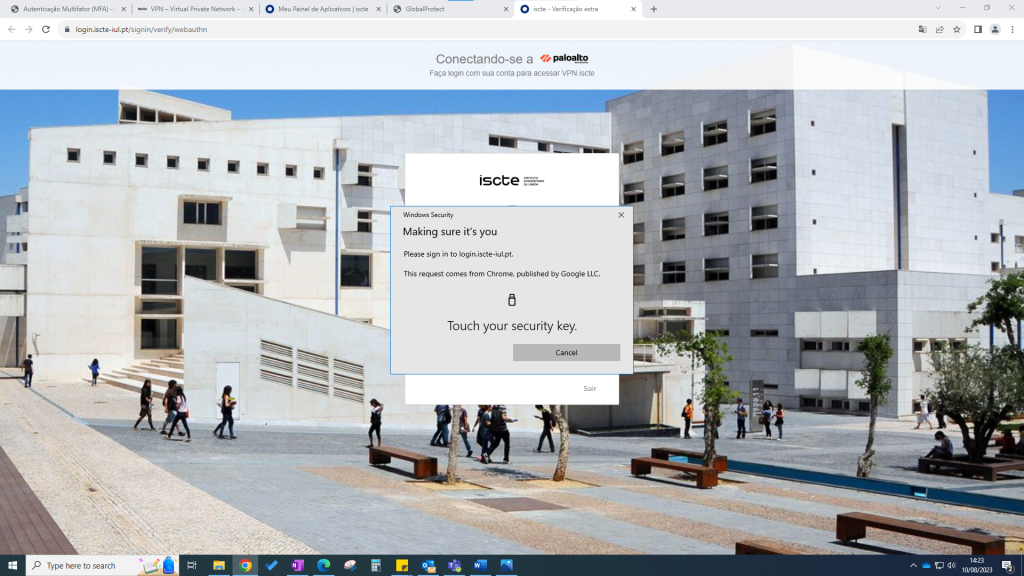
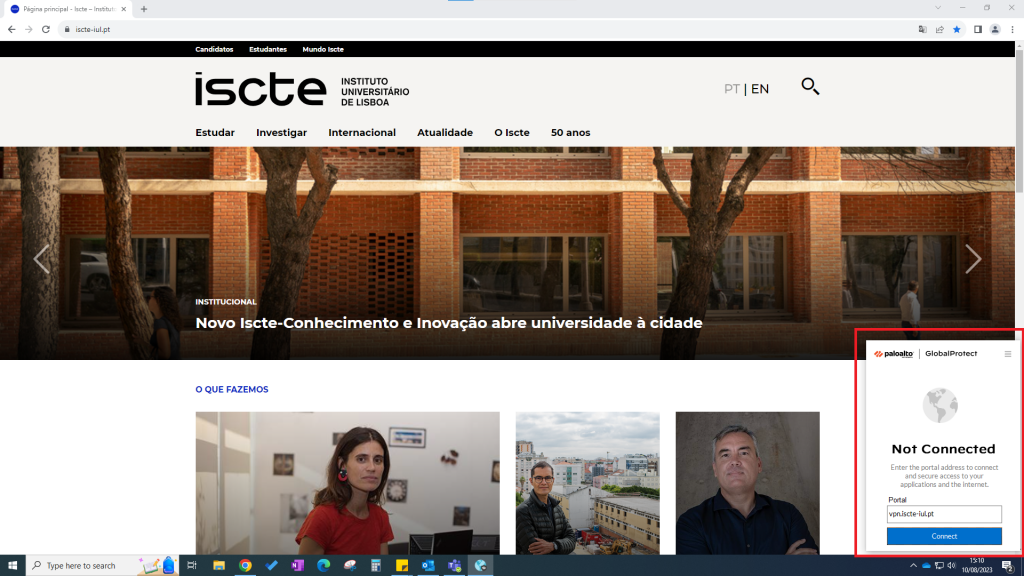
- Once the security key is configured, access GlobalProtect and in the “Welcome to Global Protect” window, in the “Please enter your portal address” field, write “vpn.iscte-iul.pt” and click on “Connect”, to establish the connection.
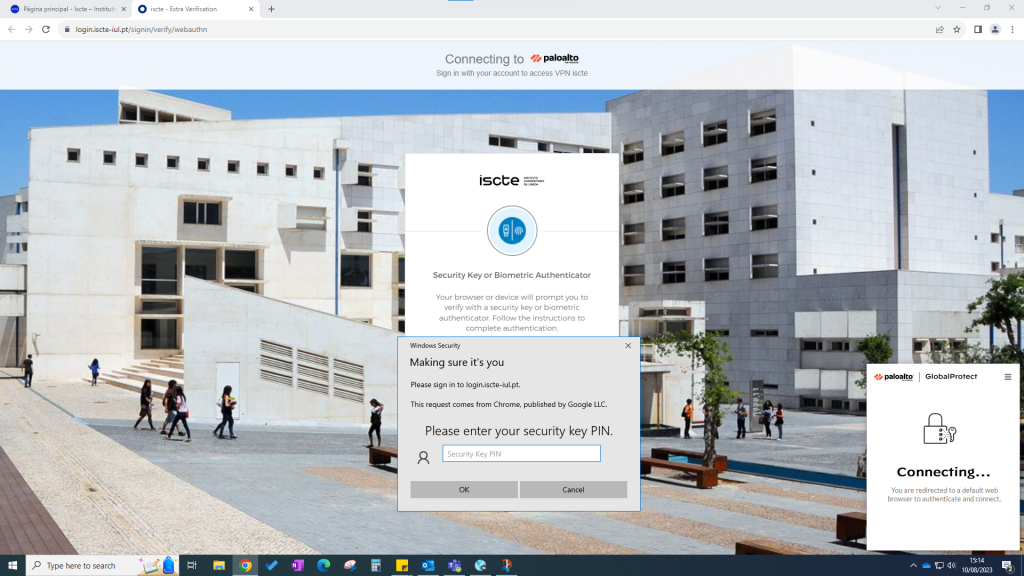
- A new window will open in the default browser where you will be asked to verify your Iscte account.
After that, you should authenticate with the security key, following the instructions to complete the authentication.
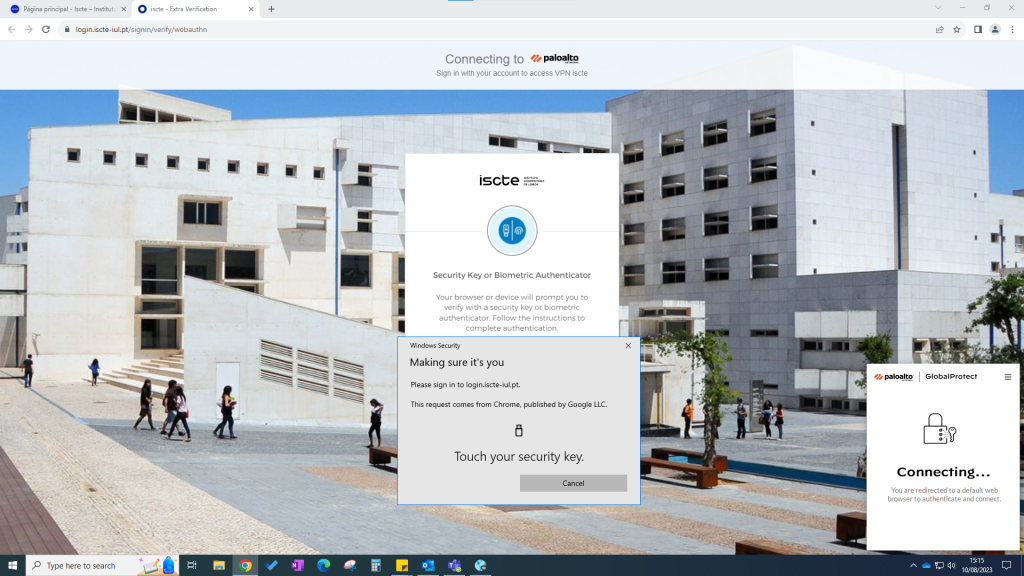
- Once authentication is complete, a new GlobalProtect tab will be displayed in the browser to establish the connection to the VPN (you can find more information on our “VPN – Virtual Private Network” webpage in the “How to install/setup VPN?” section).
- Go to https://login.iscte-iul.pt.
In the top right corner, click on the downward pointing arrow and then on “Settings“.

- In the “Security Methods” field, click on “Set up” placed in front of Google Authenticator*

*For TOTP (Time-Based One-Time Password) applications other than Okta Verify, you should always select the Google Authenticator option.
- Fill in your Iscte password.

- After filling in your password, click on Set up as in the image below.

- A QR code will be displayed. However, to make the process easier, we recommend selecting the “Can’t Scan?” option and using the code shown on the next page.
- Install a TOTP application/software on your device. When the download is complete, open and run the installation following the on-screen instructions.
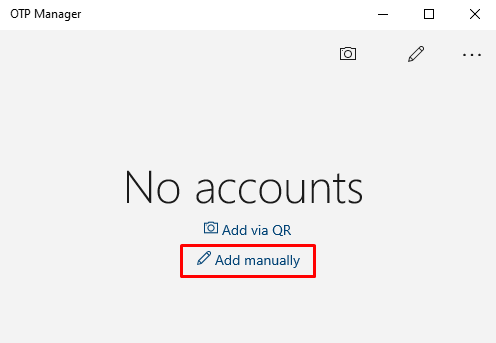
Below is an example of the OTP Manager application in the desktop version. - Open the OTP Manager application and select “Add manually”.
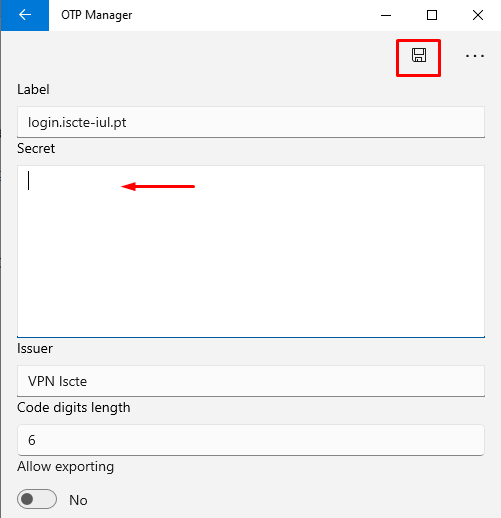
- Enter the generated code/secret key shown on the Okta website (see point 5) and save the changes.
- Enter the 6-digit code that appears in the application on the Okta website and click on “Verify“.
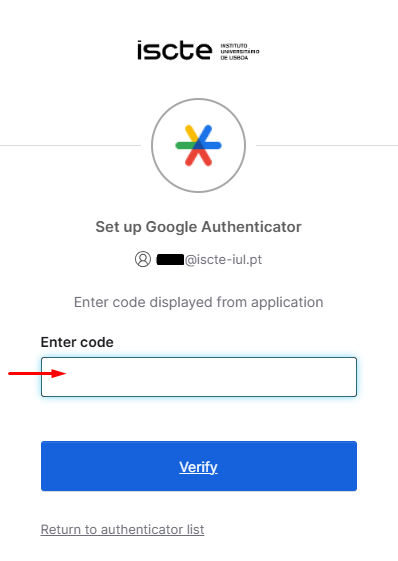
- The configuration is finished and you will be redirected to login.iscte-iul.pt page.
| App | Android | iOS | |
| Okta Verify | 9.0 or later | 16.0 or later |
| Google Authenticator | 5.0 or later | 14.0 or later |
OTP Auth | N/A | 12.0 or later | |
LastPass Authenticator | 9.0 or later | 16.0 or later | |
Twilio Authy | 6.0 or later | 15.0 or later | |
Aegis | 5.0 or later | N/A | |
Microsoft Authenticator | 8.0 or later | 15.0 or later |
| Software Desktop | Windows | macOS | Linux | |
 | OTP Manager (Aftnet) | 10 or later | N/A | N/A |
| Step Two | N/A | 13.1 or later | N/A |
